Keycloak
JBoss Keycloak 系统是一个广泛使用的开源身份管理系统,支持通过SAML和OpenID Connect与应用程序集成。 它还可以作为其他提供商(如LDAP或其他SAML提供商)和支持SAML或OpenID Connect的应用程序之间的身份代理运行。
这是一个示例,说明如何在Keycloak中配置新的客户端条目,并配置Casdoor使用它,以允许通过Keycloak配置授予访问权限的Keycloak用户进行UI登录。
Configure Keycloak
对于这个例子,让我们做出以下配置选择和假设:
- 假设你正在本地以开发模式运行Casdoor。 Casdoor UI可在
http://localhost:7001处获取,服务器可在http://localhost:8000处获取。 根据需要替换为适当的URL。 - 假设你正在本地运行Keycloak。 Keycloak UI可在
http://localhost:8080/auth处获得。 - 在此基础上,用于此部署的SPACS URL将是:
http://localhost:8000/api/acs。 - 我们的SP实体ID将使用相同的URL:
http://localhost:8000/api/acs。
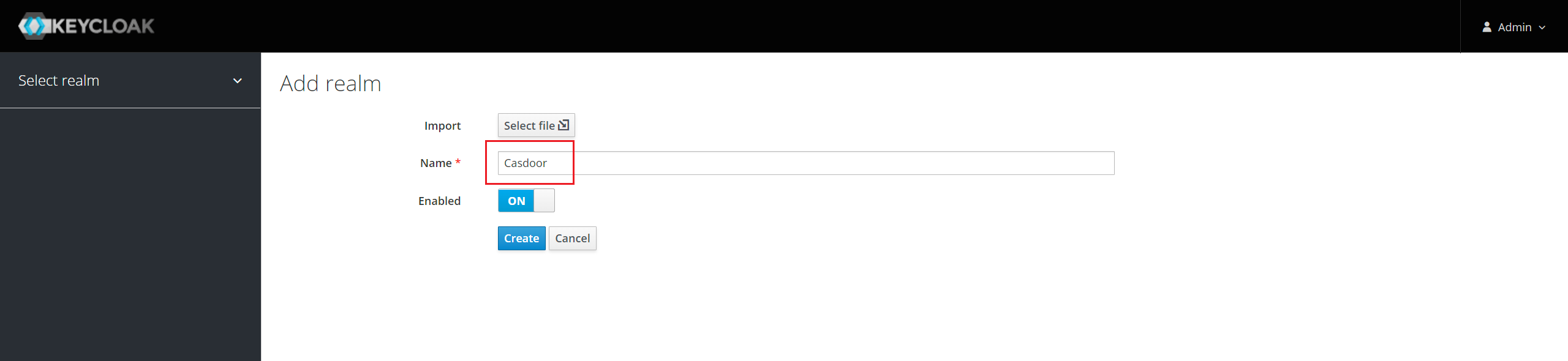
您可以使用默认的领域,或者创建一个新的领域。
在 Keycloak 中添加客户端条目
有关Keycloak Clients的更多详细信息,请参阅Keycloak文档。
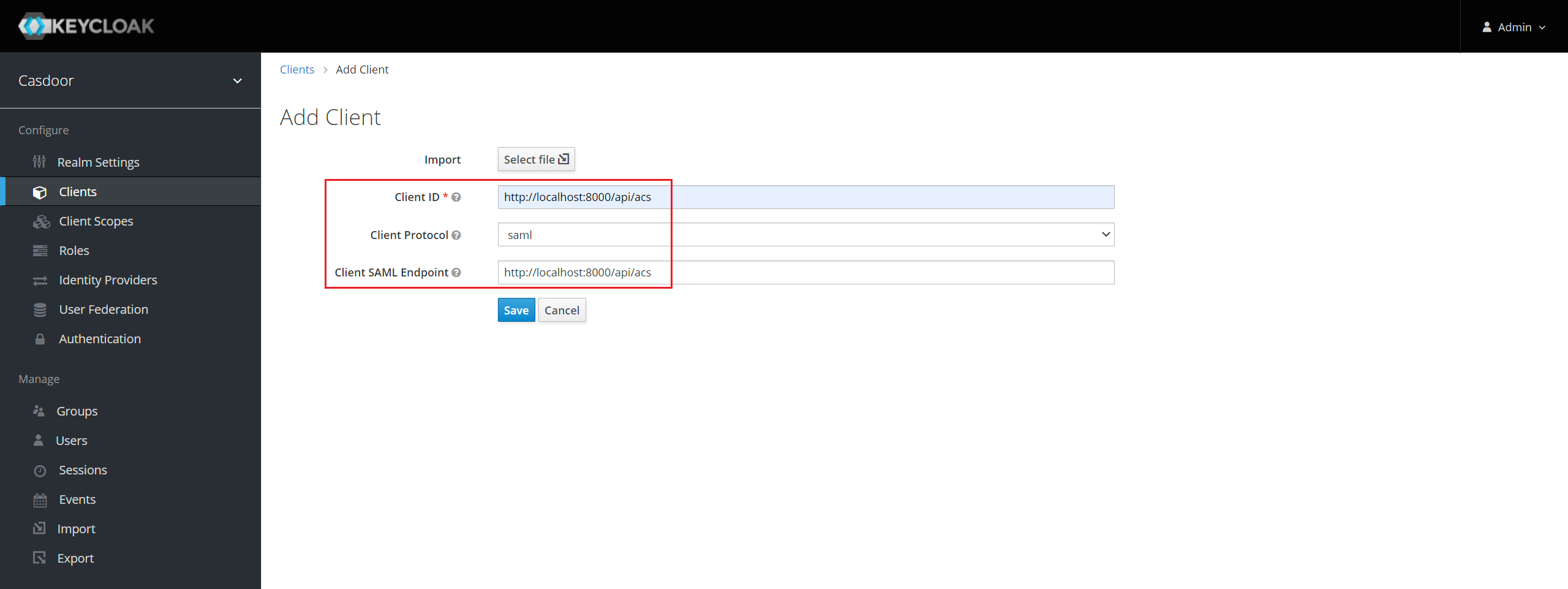
在菜单中点击 客户端 然后点击 创建 去到 添加客户端 页面。 按照以下方式填写字段:
- 客户端 ID:
http://localhost:8000/api/acs- 这将是以后在 Casdoor 配置中使用的 SP 实体ID。 - Client Protocol:
saml. - 客户端SAML端点:
http://localhost:8000/api/acs- 这个URL是你希望Keycloak服务器发送SAML请求和响应的地方。 通常,应用程序有一个用于处理SAML请求的URL。 客户端的设置选项卡中可以设置多个URL。
单击 Save(保存)。 此动作创建客户端并将您带到 设置 选项卡。
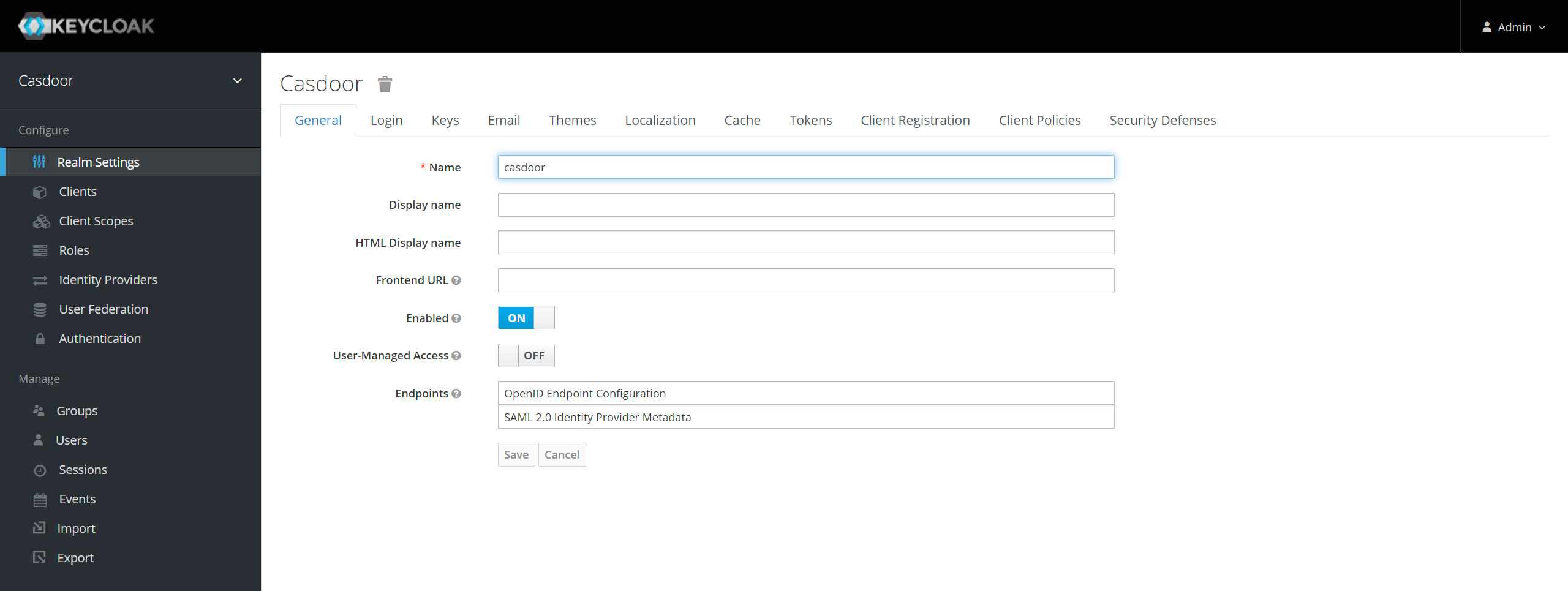
以下是设置的一部分:
- 名称 -
Casdoor. 这只用于在Keycloak用户界面中向Keycloak用户显示友好的名称。 您可以使用任何您喜欢的名字。 - 已启用 - 选择
on。 - 包含 Authn 语句 - 选择
on。 - 签署文件 - 选择
on。 - 签名断言 - 选择
off。 - 加密断言 - 选择
off。 - 需要客户签名 - 请选择
off。 - 强制名称ID格式 - 选择
on。 - 名称 ID 格式 - 选择
username。 - 有效重定向 URI - 添加
http://localhost:8000/api/acs. - Master SAML 处理 URL -
http://localhost:8000/api/acs. - 精良的谷物SAML端点配置
- 声明消费者服务公开绑定URL -
http://localhost:8000/api/acs。 - 声明消费者服务重定向绑定URL -
http://localhost:8000/api/acs。
- 声明消费者服务公开绑定URL -
保存该配置。
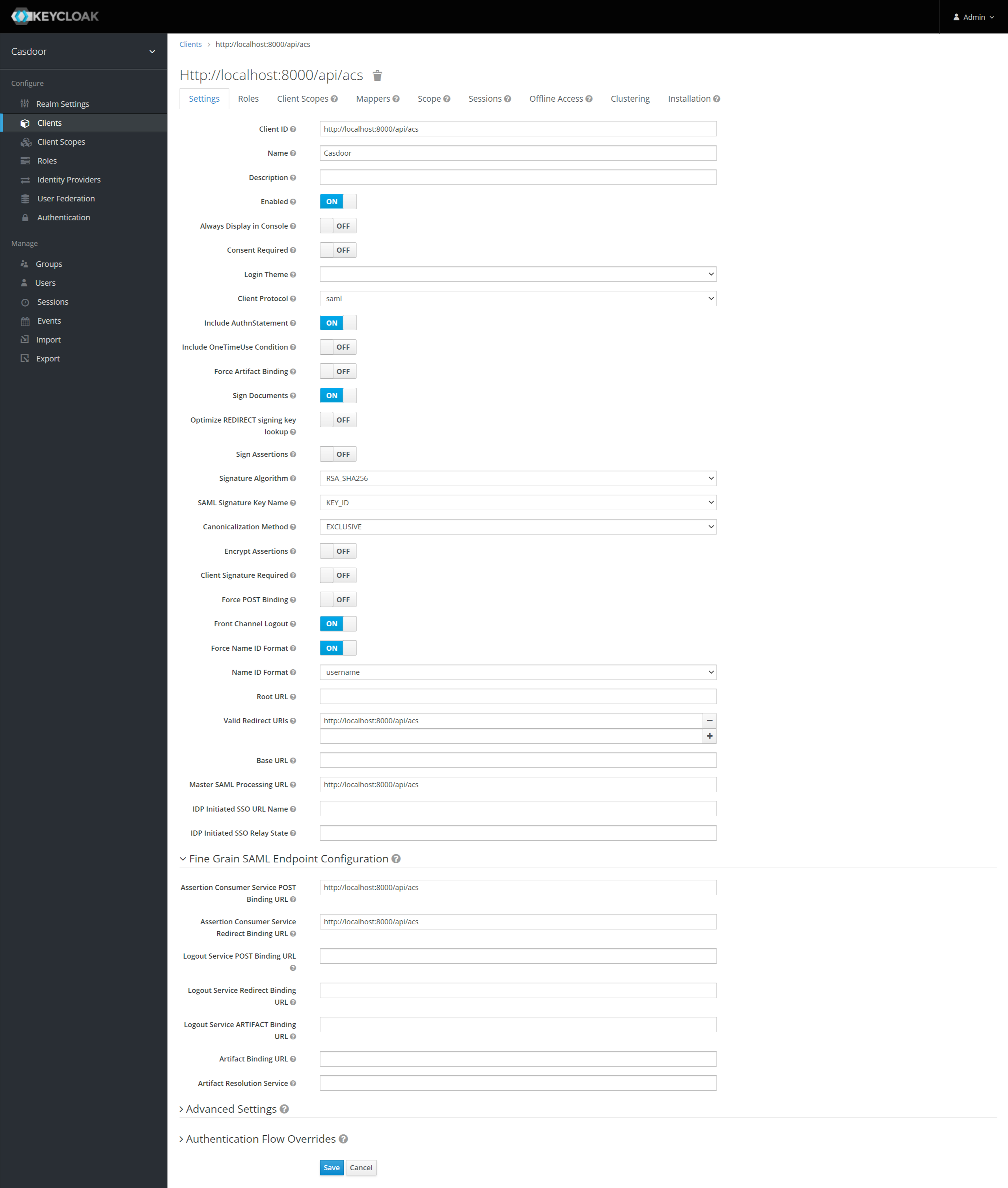
如果您想要签署authn请求,您需要启用客户端签名要求选项,并上传自己生成的证书。 在Casdoor中使用的私钥和证书,token_jwt_key.key 和 token_jwt_key.pem,位于object目录中。 在Keycloak中,您需要点击密钥选项卡,点击导入按钮,选择档案格式为证书PEM,并上传证书。
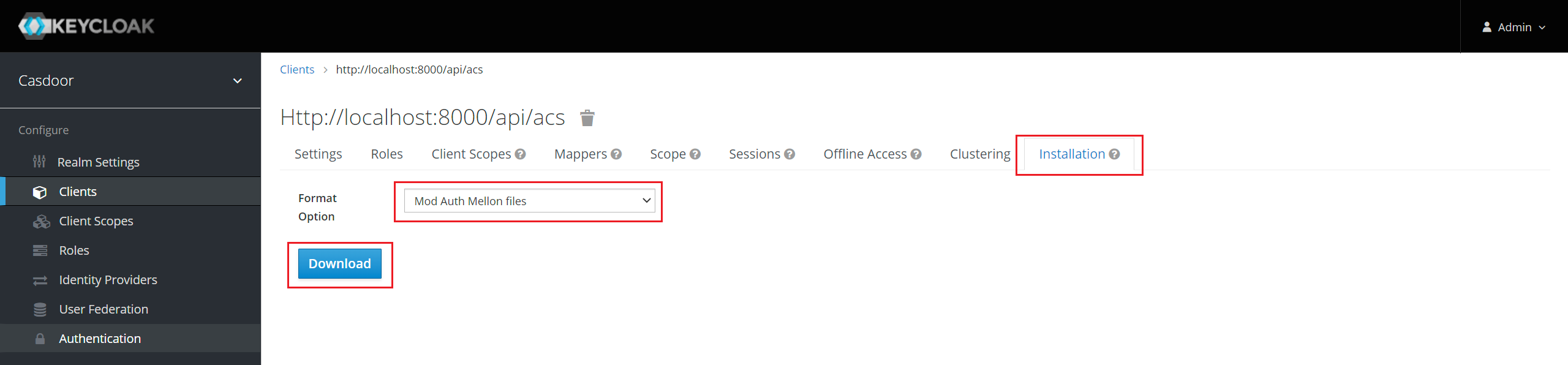
点击 安装 标签页。
对于 Keycloak <= 5.0.0,选择格式选项 - SAML Metadata IDPSSODescriptor 并复制元数据。
对于Keycloak 6.0.0+,选择格式选项 - Mod Mellon 文件 并点击 下载。 解压下载的.zip文件,找到idp-metadata.xml,并复制元数据。
在Casdoor配置
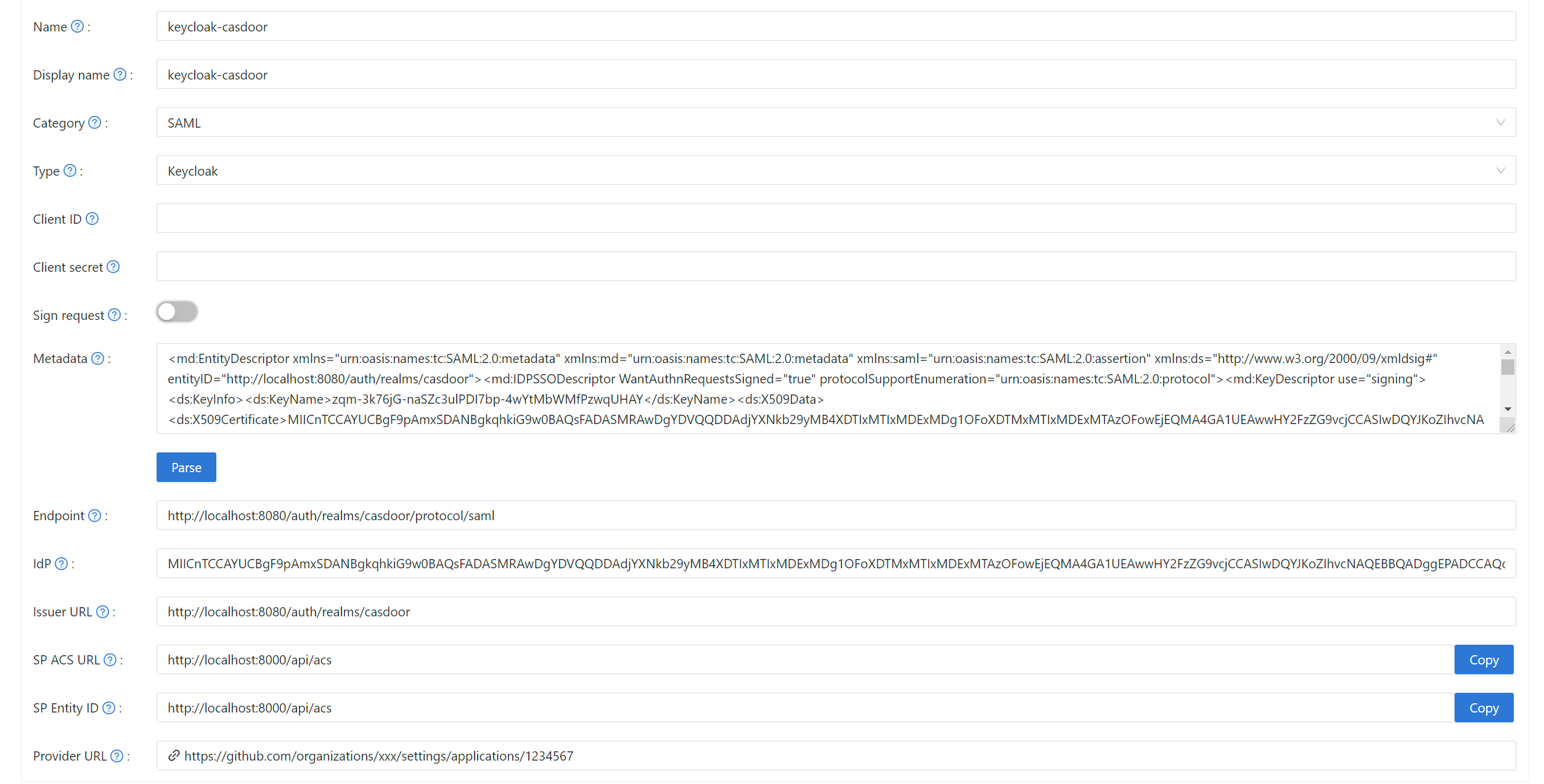
在 Casdoor 中创建一个新的提供商。
选择分类为 SAML, 输入 Keycloak. 将metadata的内容复制并粘贴到元数据字段中。 点击解析按钮后,端点、IdP和发行者URL的值将自动生成。 最后,点击保存按钮。
如果您在 Keycloak 中启用 客户端签名需要 选项并上传证书, 请在 Casdoor 中启用 签名请求 选项。
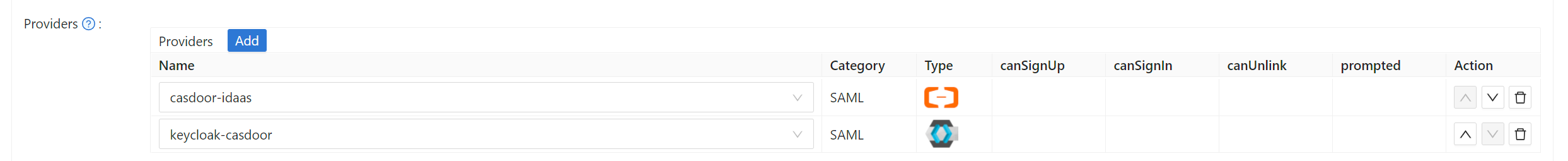
编辑您想要在 Cassdoor 中配置的应用程序。 选择你刚刚添加的提供商,然后点击保存按钮。
验证效果
转到您刚刚配置的应用程序,您会在登录页面上找到一个Keycloak图标。
点击图标,您将被重定向到Keycloak登录页面。 成功认证后,您将登录到Casdoor。
