Keycloak
JBoss Keycloakシステムは、SAMLおよびOpenID Connectを介してアプリケーションとの統合をサポートする広く使用されているオープンソースのアイデンティティ管理システムです。 LDAPや他のSAMLプロバイダーとの間でアイデンティティブローカーとしても機能し、SAMLまたはOpenID Connectをサポートするアプリケーションと統合できます。
Keycloakで新しいクライアントエントリを設定し、Keycloakの設定を通じてアクセスを許可されたKeycloakユーザーがUIログインできるようにCasdoorを設定する方法の例を以下に示します。
Keycloakの設定
この例では、以下の設定選択と仮定を行います:
- Casdoorをローカルで開発モードで実行していると仮定します。 Casdoor UIは
http://localhost:7001で利用可能で、サーバーはhttp://localhost:8000で利用可能です。 必要に応じて適切なURLに置き換えてください。 - Keycloakをローカルで実行していると仮定します。 Keycloak UIは
http://localhost:8080/authで利用可能です。 - それに基づいて、このデプロイメントのSP ACS URLは次のようになります:
http://localhost:8000/api/acs。 - SPエンティティIDは同じURLを使用します:
http://localhost:8000/api/acs。
The /api/acs endpoint only accepts POST requests. Ensure Keycloak is configured to use HTTP POST binding for SAML responses.
デフォルトのレルムを使用するか、新しいレルムを作成することができます。
Keycloakにクライアントエントリを追加
Keycloakクライアントの詳細については、Keycloakドキュメントを参照してください。
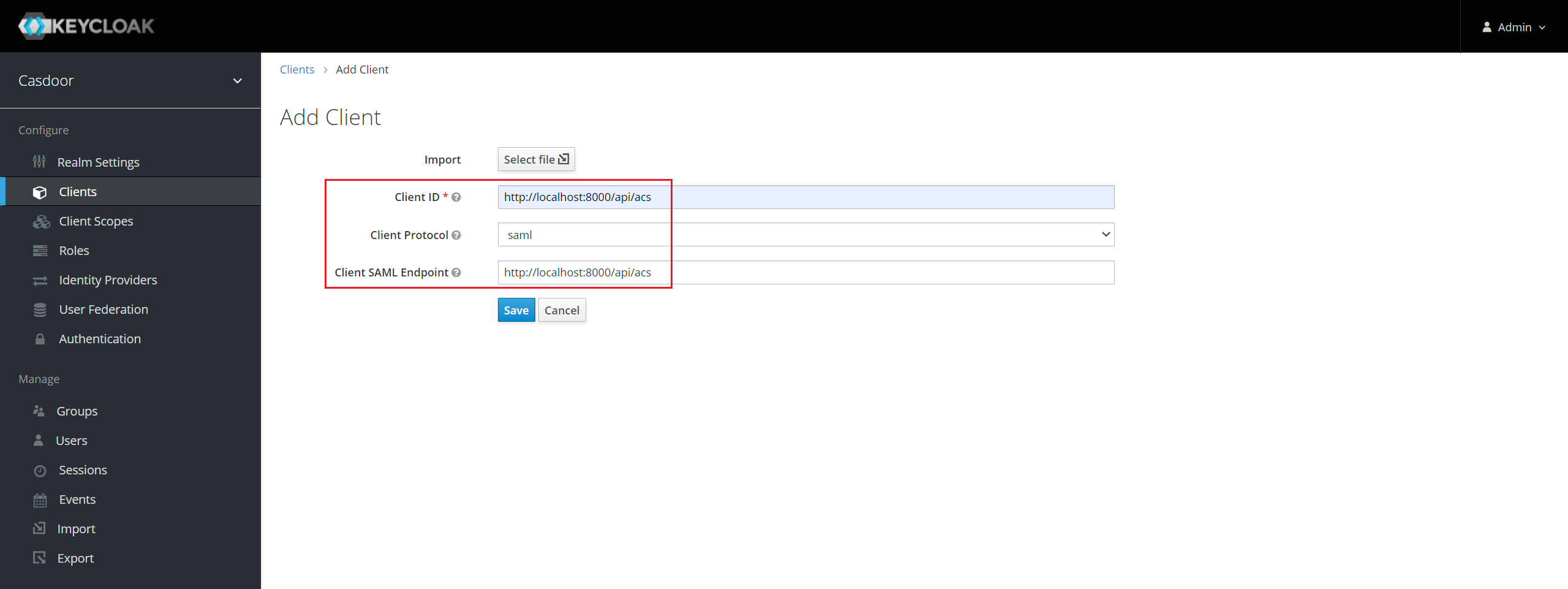
メニューのクライアントをクリックし、次に作成をクリックしてクライアント追加ページに進みます。 以下のようにフィールドを入力します:
- クライアントID:
http://localhost:8000/api/acs- これは後でCasdoor設定で使用されるSPエンティティIDになります。 - クライアントプロトコル:
saml。 - クライアントSAMLエンドポイント:
http://localhost:8000/api/acs- このURLは、KeycloakサーバーがSAMLリクエストとレスポンスを送信する場所です。 一般的に、アプリケーションはSAMLリクエストを処理するための1つのURLを持っています。 複数のURLはクライアントの設定タブで設定できます。
保存をクリック。 このアクションはクライアントを作成し、設定タブに移動します。
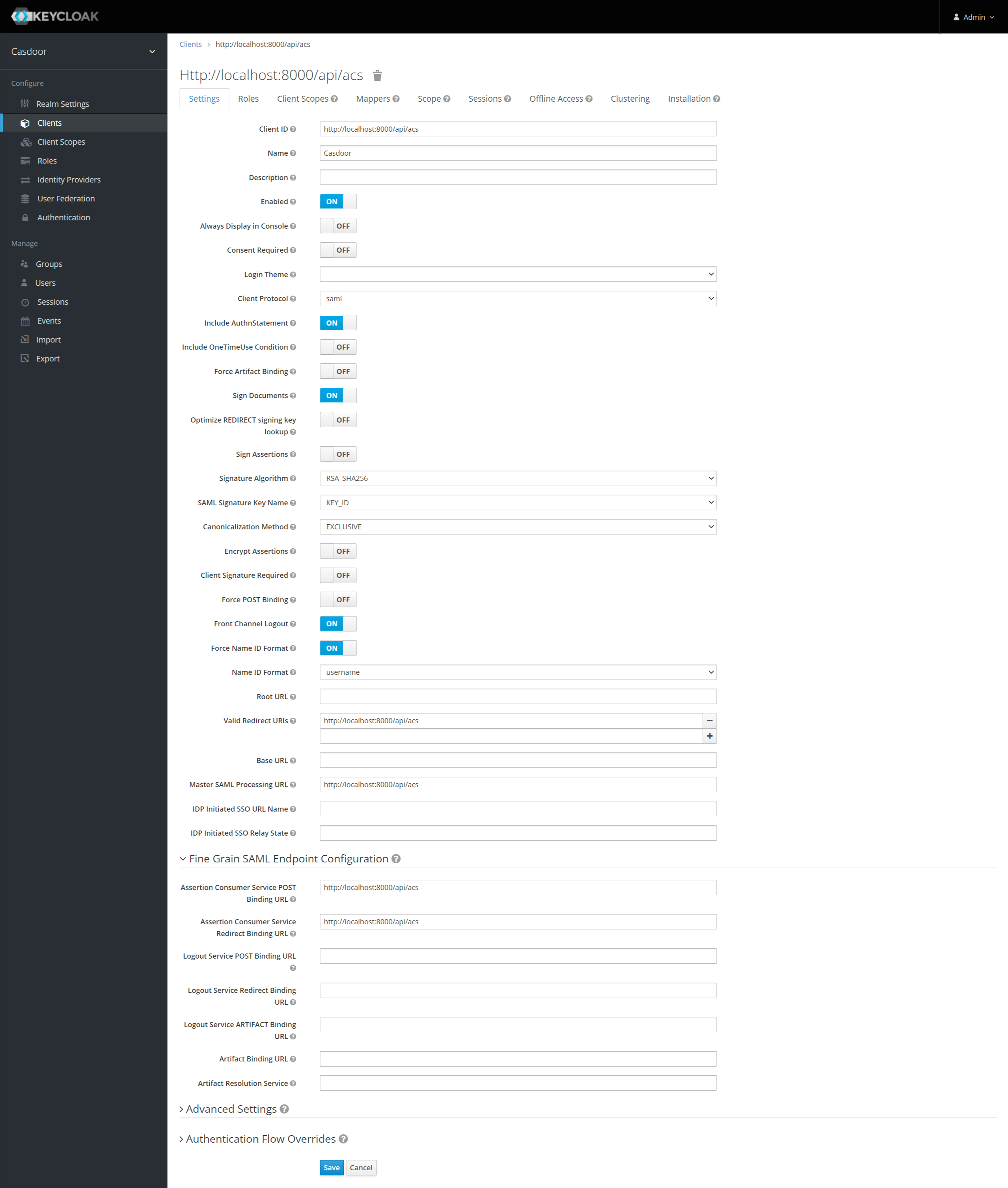
設定の一部は以下の通りです:
- 名前 -
Casdoor。 これはKeycloak UIでKeycloakユーザーにフレンドリーな名前を表示するためにのみ使用されます。 好きな名前を使用できます。 - 有効 -
onを選択。 - Authnステートメントを含む -
onを選択。 - ドキュメントに署名 -
onを選択。 - アサーションに署名 -
offを選択。 - アサーションを暗号化 -
offを選択。 - クライアント署名必須 -
offを選択。 - Name IDフォーマットを強制 -
onを選択。 - Name IDフォーマット -
usernameを選択。 - 有効なリダイレクトURI -
http://localhost:8000/api/acsを追加。 - マスターSAML処理URL -
http://localhost:8000/api/acs。 - 細かいSAMLエンドポイント設定
- アサーションコンシューマーサービスPOSTバインディングURL -
http://localhost:8000/api/acs。 - アサーションコンシューマーサービスリダイレクトバインディングURL -
http://localhost:8000/api/acs。
- アサーションコンシューマーサービスPOSTバインディングURL -
設定を保存する。
authnリクエストに署名する場合は、クライアント署名必須オプションを有効にし、自分で生成した証明書をアップロードする必要があります。 Casdoorで使用される秘密鍵と証明書、token_jwt_key.keyとtoken_jwt_key.pemは、objectディレクトリにあります。 Keycloakでは、鍵タブをクリックし、インポートボタンをクリックし、アーカイブフォーマットとして証明書PEMを選択し、証明書をアップロードする必要があります。
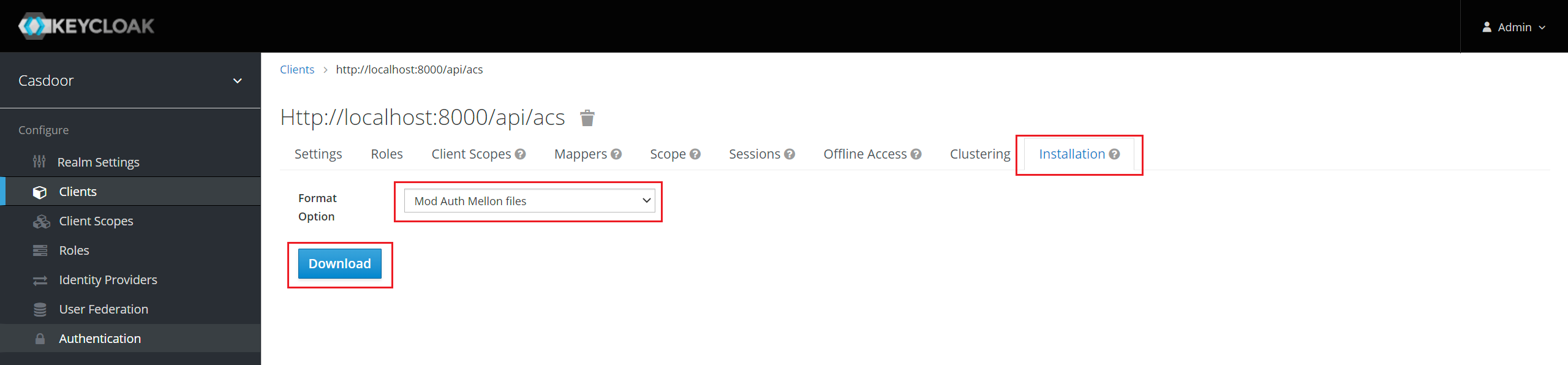
インストールタブをクリック。
Keycloak <= 5.0.0の場合、フォーマットオプション - SAML Metadata IDPSSODescriptorを選択し、メタデータをコピーします。
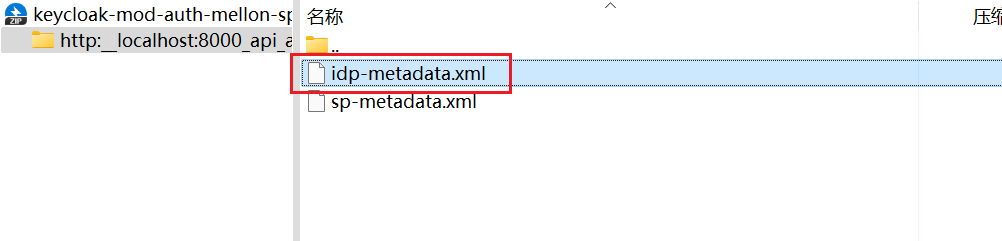
Keycloak 6.0.0+の場合、フォーマットオプション - Mod Auth Mellon filesを選択し、ダウンロードをクリック。 ダウンロードした.zipを解凍し、idp-metadata.xmlを探してメタデータをコピーします。
Casdoorでの設定
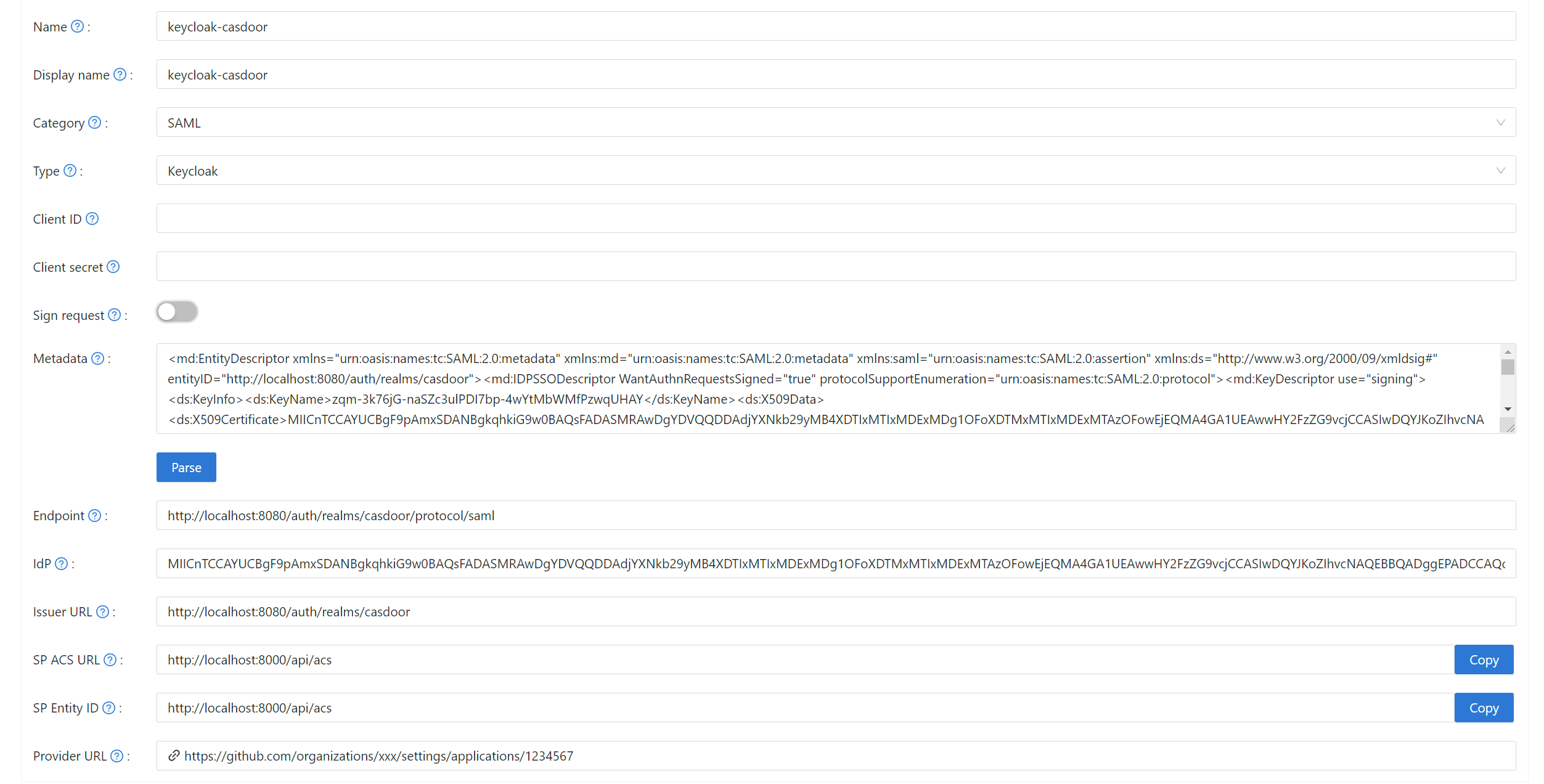
Casdoorに新しいプロバイダーを作成。
カテゴリをSAML、タイプをKeycloakとして選択。 メタデータの内容をコピーして、メタデータフィールドに貼り付けます。 エンドポイント、IdP、発行者URLの値は、解析ボタンをクリックした後に自動的に生成されます。 最後に、保存ボタンをクリックします。
Keycloakでクライアント署名必須オプションを有効にし、証明書をアップロードした場合、Casdoorでリクエストに署名オプションを有効にしてください。
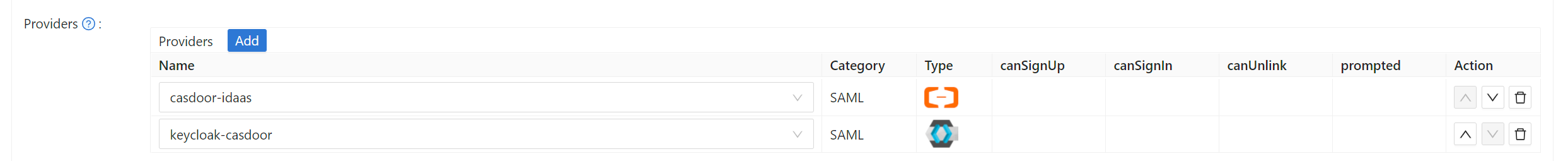
Casdoorで設定したいアプリケーションを編集。 追加したばかりのプロバイダーを選択し、保存ボタンをクリックします。
効果を検証する
設定したばかりのアプリケーションに移動すると、ログインページにKeycloakアイコンが表示されます。
アイコンをクリックすると、Keycloakのログインページにリダイレクトされます。 認証に成功すると、Casdoorにログインされます。
