Appgate (POST)
在Appgate中的Casdoor作为SAML IdP
Appgate accepte SAMLResponse 由 POST 请求发送。 如果您使用另一个也支持POST 请求的服务供应商(SP),您可以引用此文档。
Casdoor 配置
转到您的 Casdoor 帐户并添加一个新的应用程序。
在应用程序中输入基本的 SAML 配置:
重定向URLs:输入一个唯一的名称。 在您的SP中,这可能被称为
Audience或Entity ID。 见下表。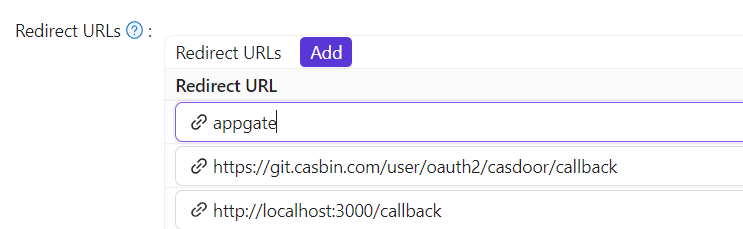
Reply URL–键入验证SAML响应的ACS(声明消费者服务)的URL。 请参阅下表。
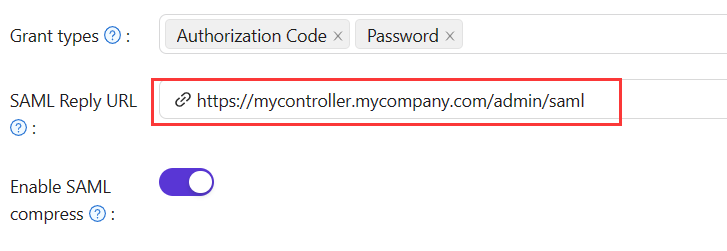
| 管理员验证 | 用户认证 |
|---|---|
| 重定向URL = "AppGate" | 重定向URL = "AppGate Client" |
| SAML回复URL = https://mycontroller.your-site-url.com/admin/saml | SAML回复URL = https://redirectserver.your-site-url.com/saml |
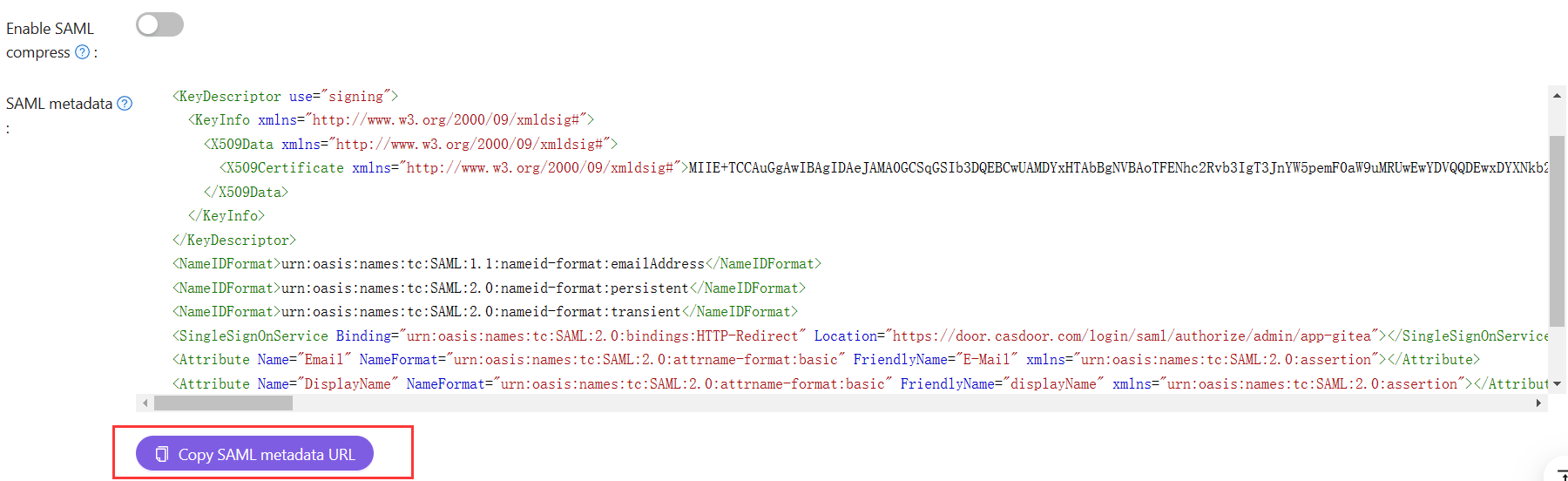
下载XML元数据文件
您可以复制元数据的URL,并从浏览器下载文件。
在Appgate中添加SAML IdP
在您的AppGate SDP控制台:
选择系统 > 身份提供商。
创建一个新的身份提供商。
选择SAML类型。
按照下表中的详细信息开始配置您的身份提供程序。
| 管理员验证 | |
|---|---|
| 姓名 | 输入一个唯一的名称,例如“Casdoor SAML Admin”。 |
| 单点登录URL | 见下文 |
| 发行人 | 见下文 |
| 受众 | 在Casdoor应用中输入重定向URL |
| 公共证书 | 见下文 |
上传XML元数据文件以自动完成单点登录、发行人和公共证书字段。
点击选择文件并选择您之前下载的元数据文件 - 这将自动完成相关字段。
映射属性
将名称映射到用户名。 您完成的表格应该看起来像这样:
测试集成
在您的AppGate SDP控制器控制台:
退出管理员界面。
使用以下信息登录:
身份提供商 - 从下拉列表中选择您的Azure IdP。
点击用浏览器登录以连接到您的验证器。
您可能会看到以下消息: "您没有任何管理权限" - 这确认了测试用户凭据已经被您的身份提供商成功验证。
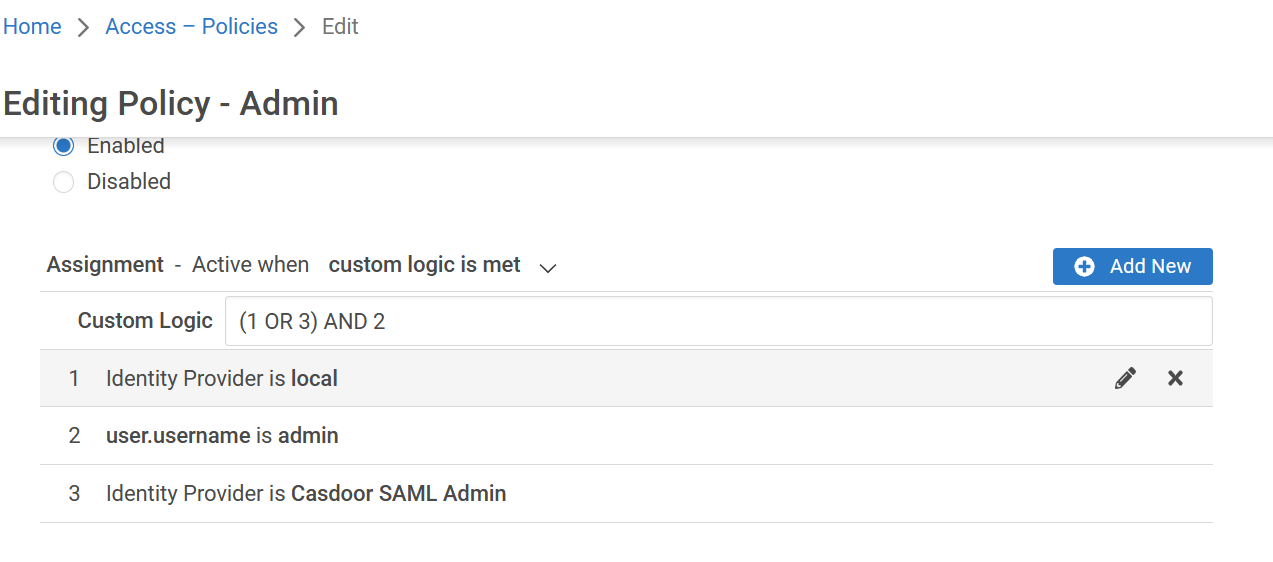
访问策略
您需要修改访问策略,以允许管理员使用SAML IdP登录到Appgate。 输入内置管理员策略:
您完成的表格应该看起来像这样: