개요
Casdoor는 OAuth를 기반으로 하며, 사용자의 OAuth 토큰으로 토큰을 사용합니다.
Access Token and ID Token
In Casdoor, the access_token and id_token are identical. Both tokens contain the same JWT payload with user information and claims. This is a design choice in Casdoor that simplifies token management.
This approach means:
- Both tokens contain the same user information and custom claims
- Both tokens can be used interchangeably for authentication and authorization
- The token format and expiration settings apply to both tokens equally
- You cannot configure separate claims for
access_tokenandid_token
Token Fields
Casdoor에서 사용 가능한 토큰 필드는 다음과 같습니다:
OwnerNameCreatedTimeApplicationOrganizationUserCodeAccessTokenExpireIn(토큰은 시간 후에 만료됩니다)Scope(권한 범위)TokenType(예,Bearer타입)
응용 프로그램에 로그인 한 후, JWT 토큰을 생성하는 세 가지 옵션이 있습니다:
JWTJWT-EmptyJWT-CustomJWT-Standard
옵션은 다음과 같습니다: JWT는 모든 사용자 필드를 포함한 토큰을 생성하고, JWT-Empty는 사용자의 모든 비어 있지 않은 값에 대한 토큰을 생성하며, JWT-Custom은 사용자 지정 사용자 토큰 필드를 포함한 토큰을 생성합니다 (토큰 필드에서 속성을 선택할 수 있습니다). JWT-Standard will generate a token with some standard OIDC token fields include email, phone, gender and Address (Address value in other format is not standard).
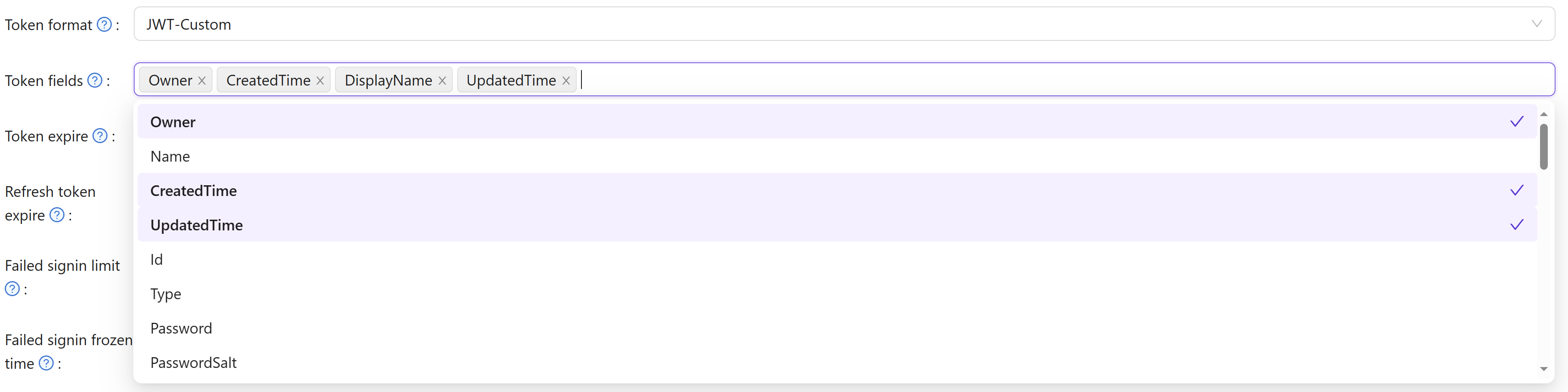
Custom Token Attributes
When using JWT-Custom format, you can define custom attributes with their data types. Each attribute has a Type field that controls how values are included in the JWT:
- Array: The attribute value will always be returned as an array, even if it contains a single element. This ensures compatibility with OIDC clients that expect array types for fields like roles, groups, or permissions.
- String: The attribute value will be returned as a single string (the first element if multiple values exist).
Empty attributes are automatically omitted from the token to keep the payload clean. When configuring attributes for roles, groups, or permissions, using the Array type is recommended for better OIDC compliance and compatibility with systems like Rancher and Keycloak.