AWS Client VPN
Casdoor as a SAML IdP in AWS Client VPN
This guide will show you how to configure Casdoor and AWS Client VPN to add Casdoor as a SAML IdP in AWS Client VPN.
Prerequisites
To complete this setup, you will need:
An AWS Account with administrative rights to access configuration settings of the service provider.
An Amazon VPC with an EC2 instance
- Setting up the VPC
- Launching an EC2 instance
- In the instance Security Group, allow ICMP traffic from the VPC CIDR range - this is needed for testing.
A private certificate imported into AWS Certificate Manager (ACM)
A Windows or Mac system running the latest AWS Client VPN software.
Configure SAML Application
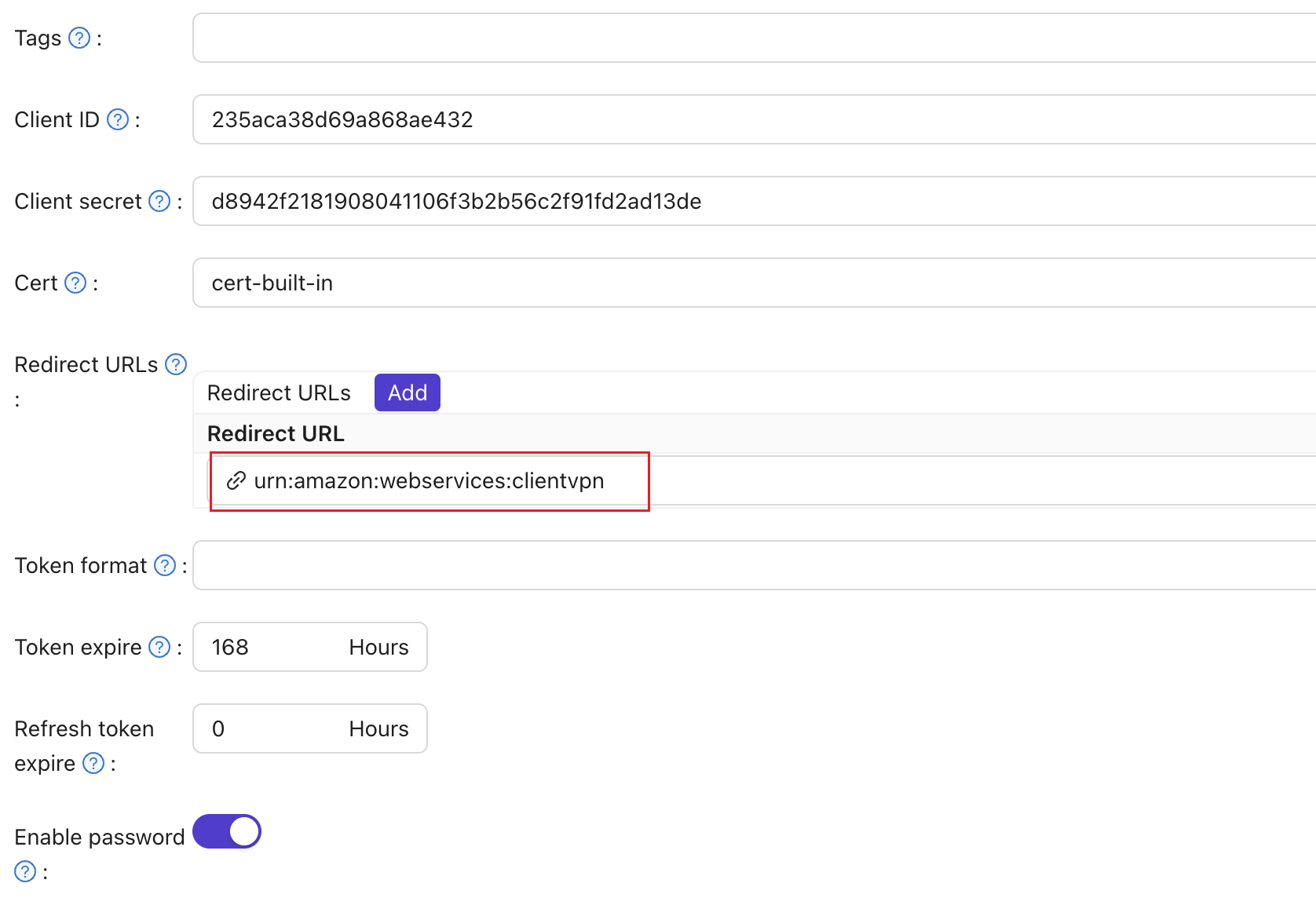
- In the Casdoor Application, set the
Redirect URLtourn:amazon:webservices:clientvpn.
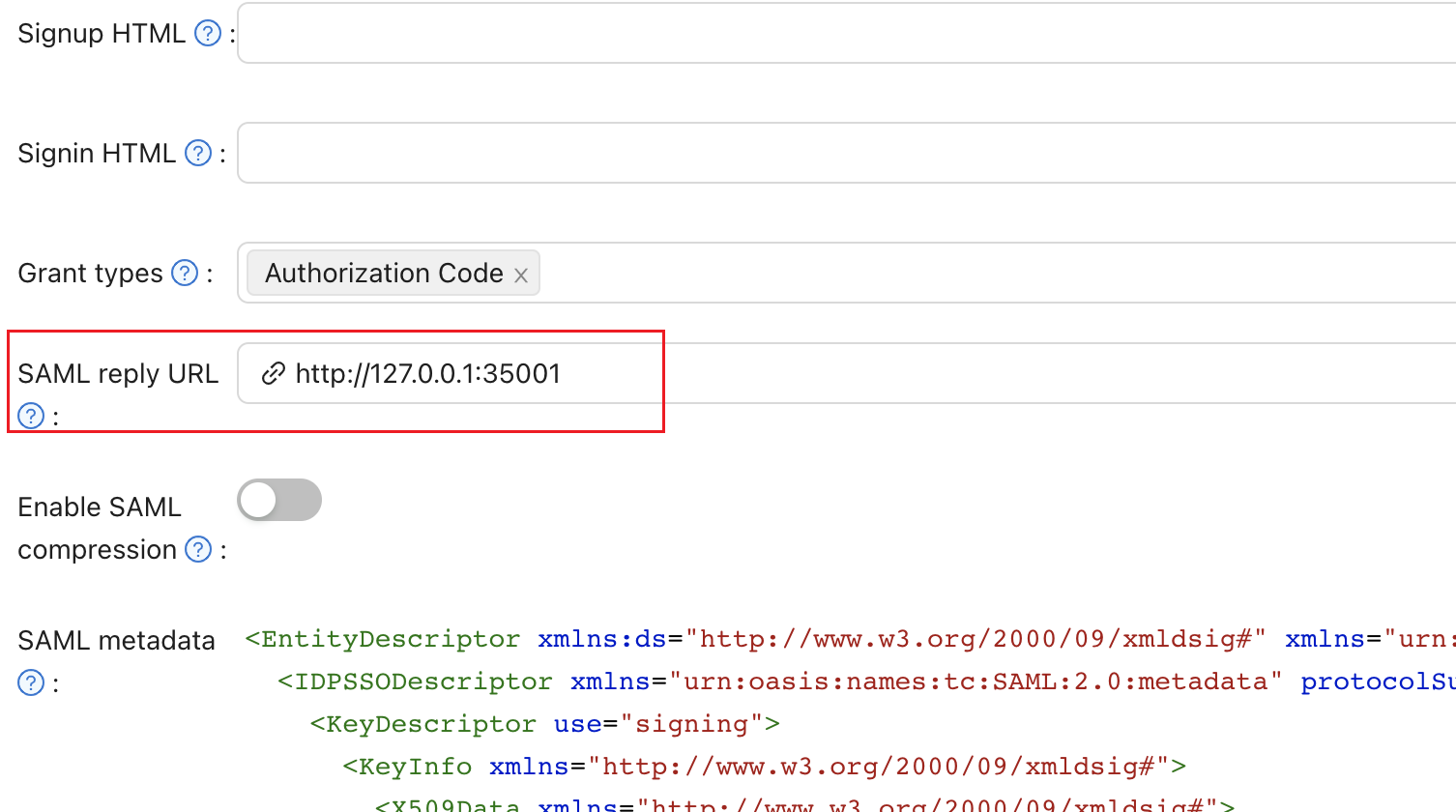
- Set the
SAML reply URLtohttp://127.0.0.1:35001.
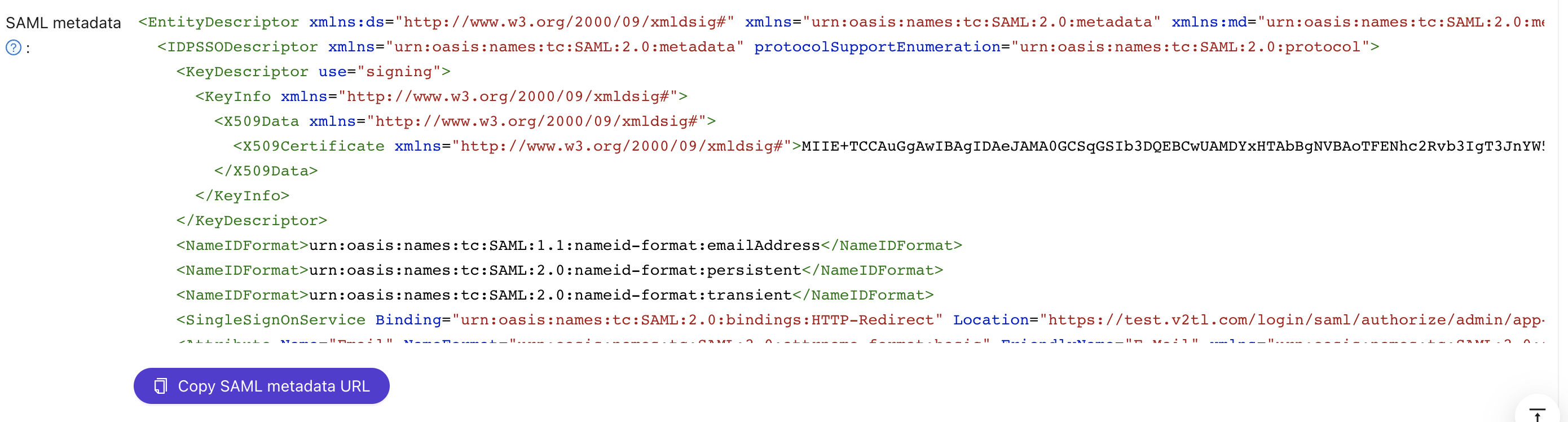
- Save the content in the
SAML metadataas an XML file.
Configure AWS
Configure Casdoor as an AWS Identity Provider
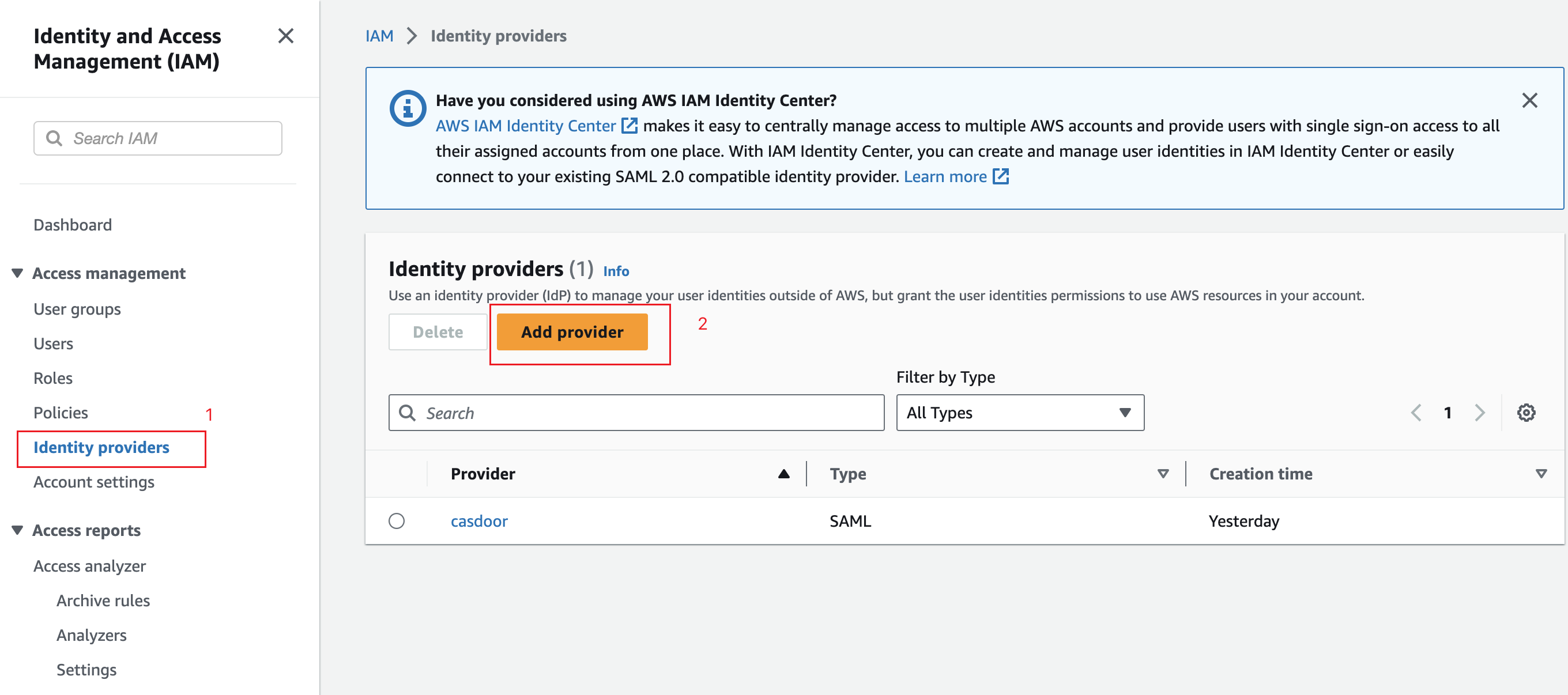
Open the IAM console and select Identity providers from the navigation bar.
Click Create a Provider.
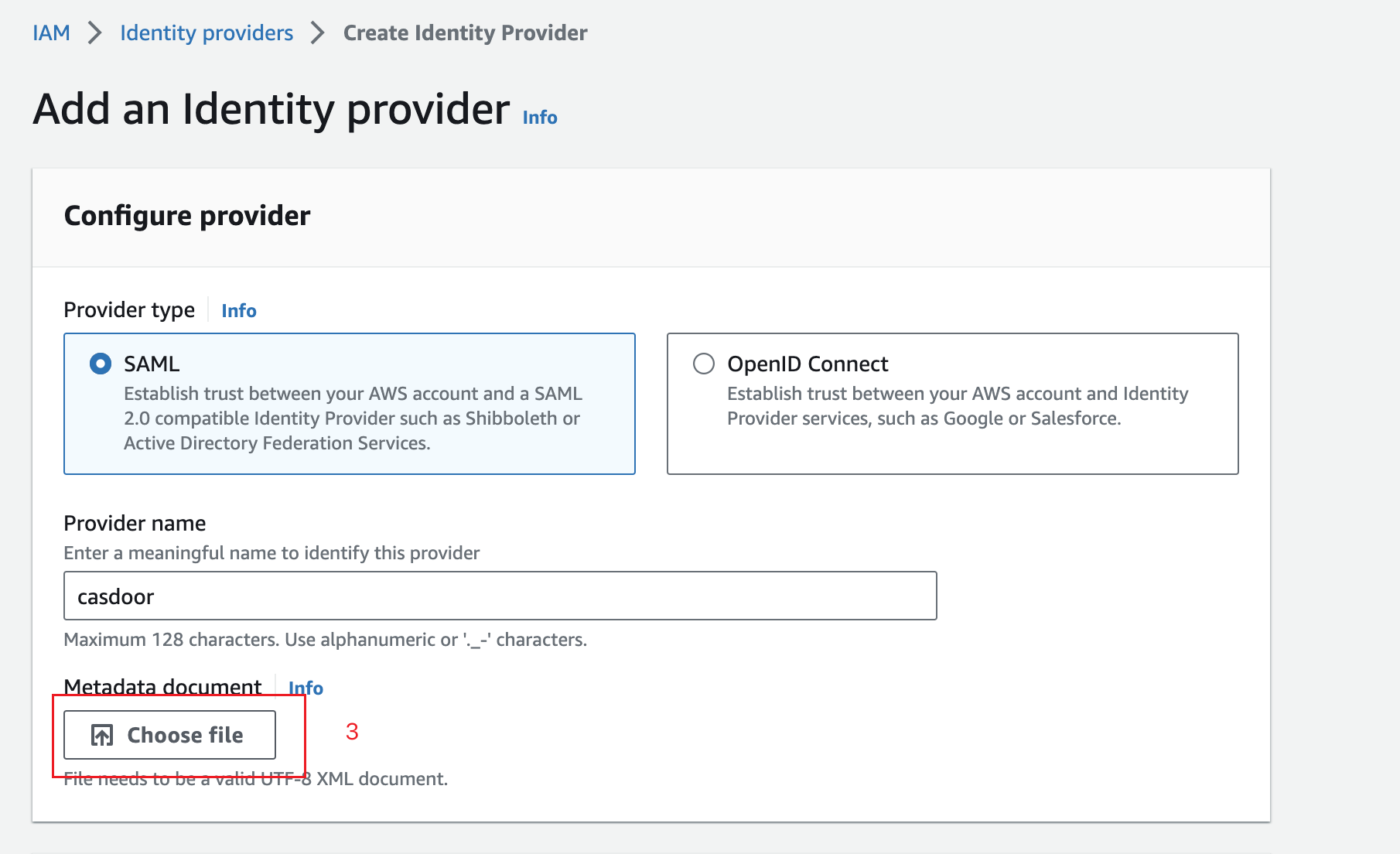
Specify SAML for the Provider Type, add a unique name for this provider, and upload the metadata document - the same file you saved from the Casdoor Application in the previous section.
Click Next Step. On the next screen, click Create.
Create an AWS Client VPN Endpoint
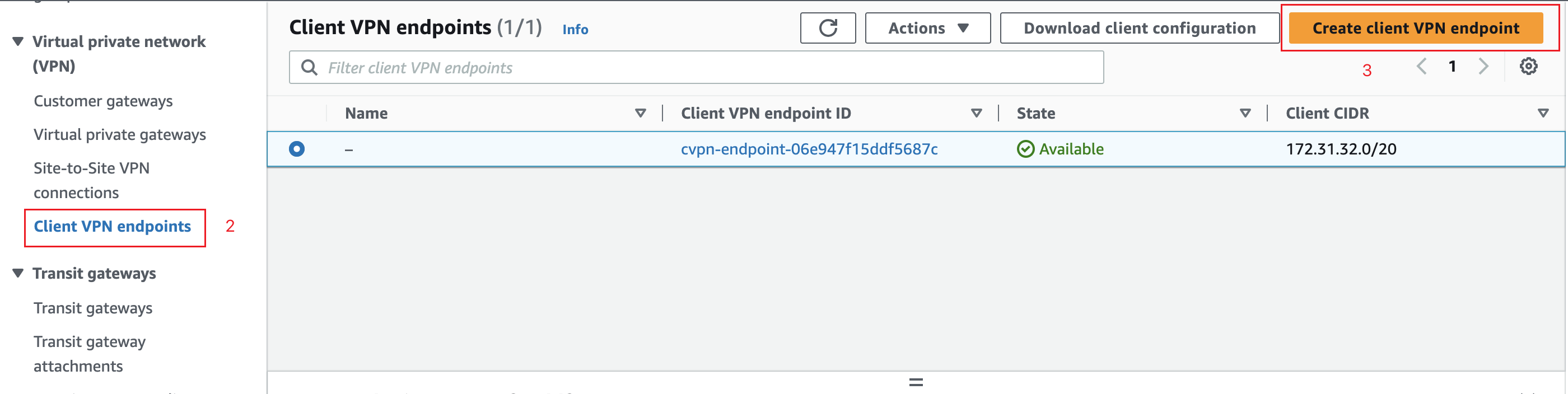
Open the Amazon VPC console in an AWS Region of your choice.
On the left-hand side navigation, select Client VPN Endpoints under Virtual Private Network (VPN).
Click Create Client VPN Endpoint.
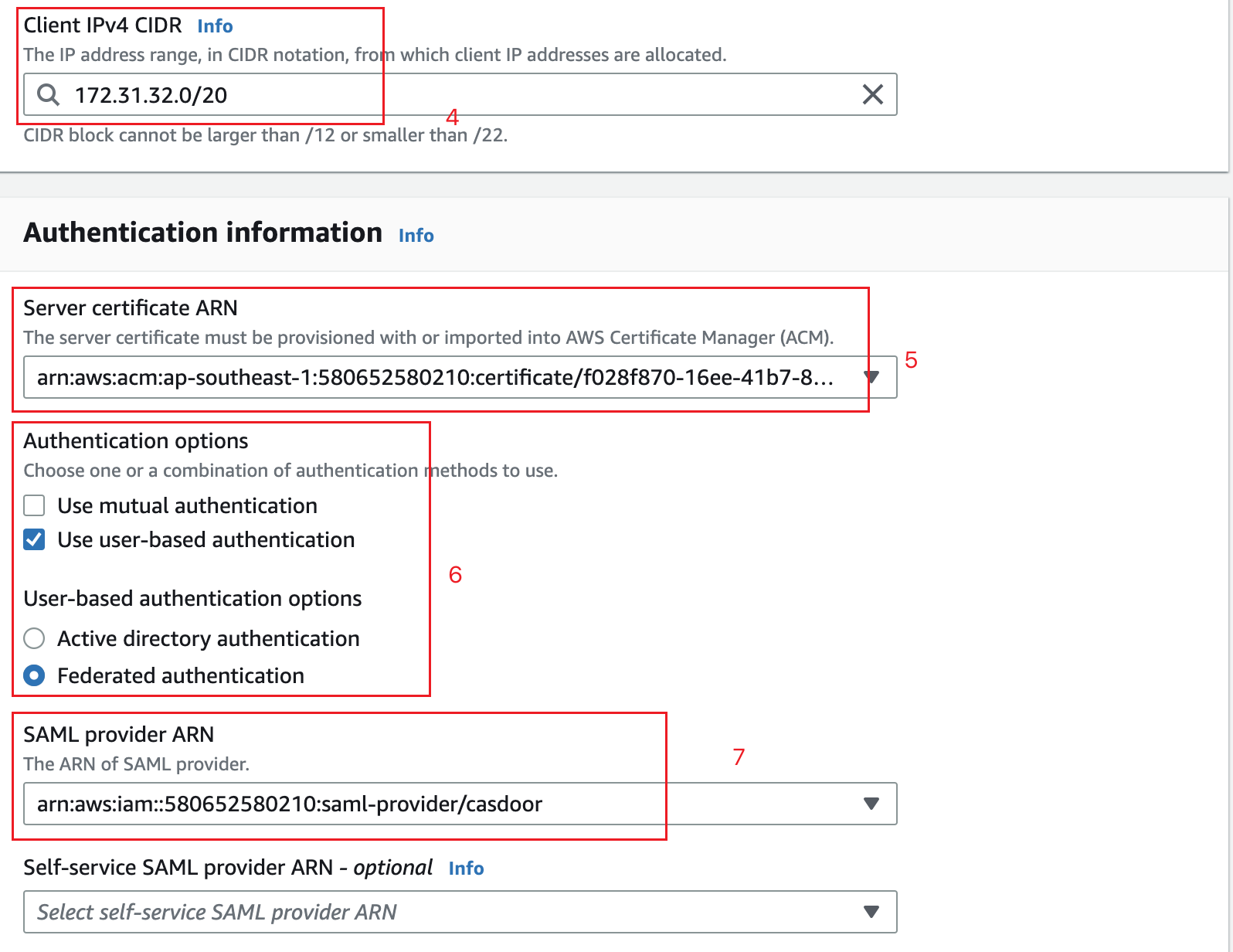
Enter the IP range for your remote users in the Client IPv4 CIDR field to allocate an IP range.
For Server Certificate ARN, select the certificate you created.
For Authentication Options, select Use user-based authentication, then Federated authentication.
For SAML provider ARN, select the identity provider you created.
Click Create Client VPN Endpoint.
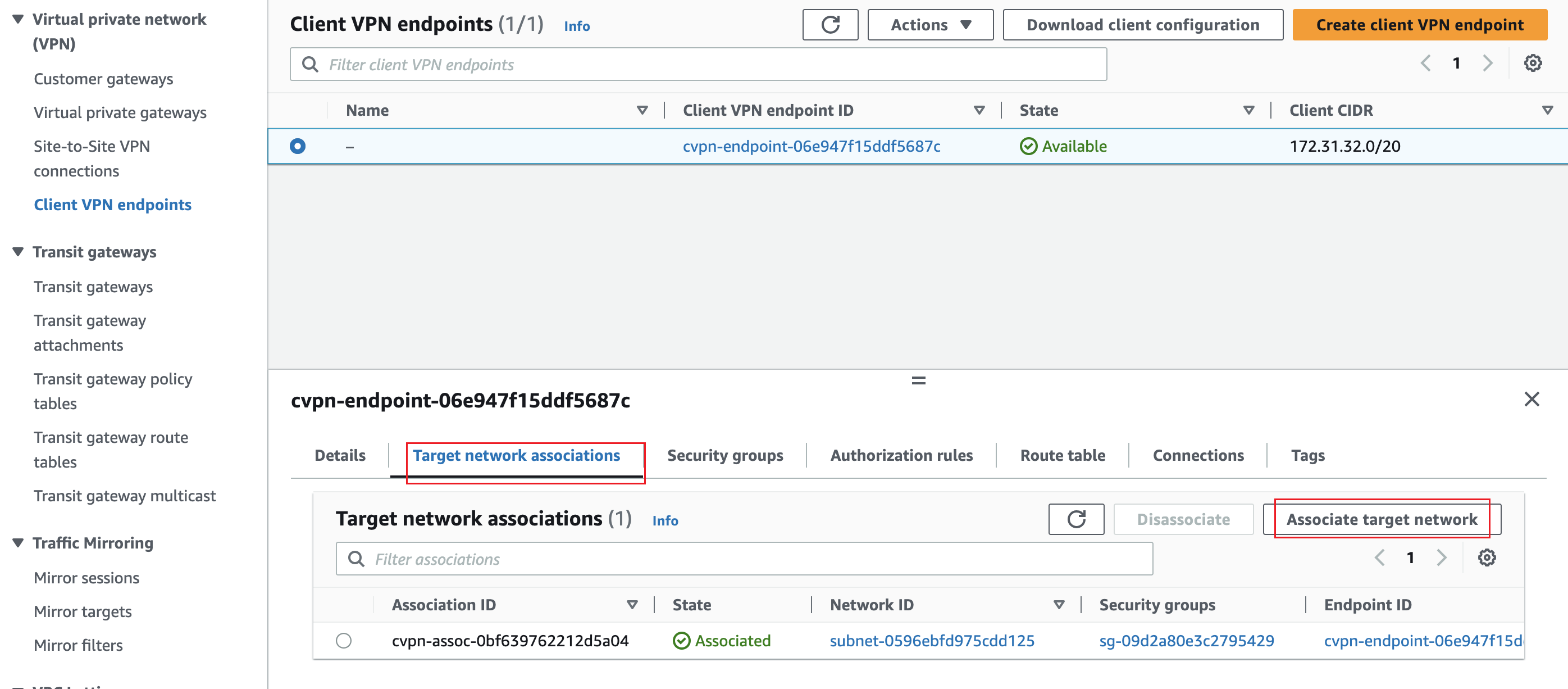
Associate a Client VPN with a Target VPC
Select Target network associations in the Client VPN options, then click Associate target network.
From the drop-down menu, select the target VPC and subnet you want to associate your endpoint with.
Configure SAML Group-Specific Authorization
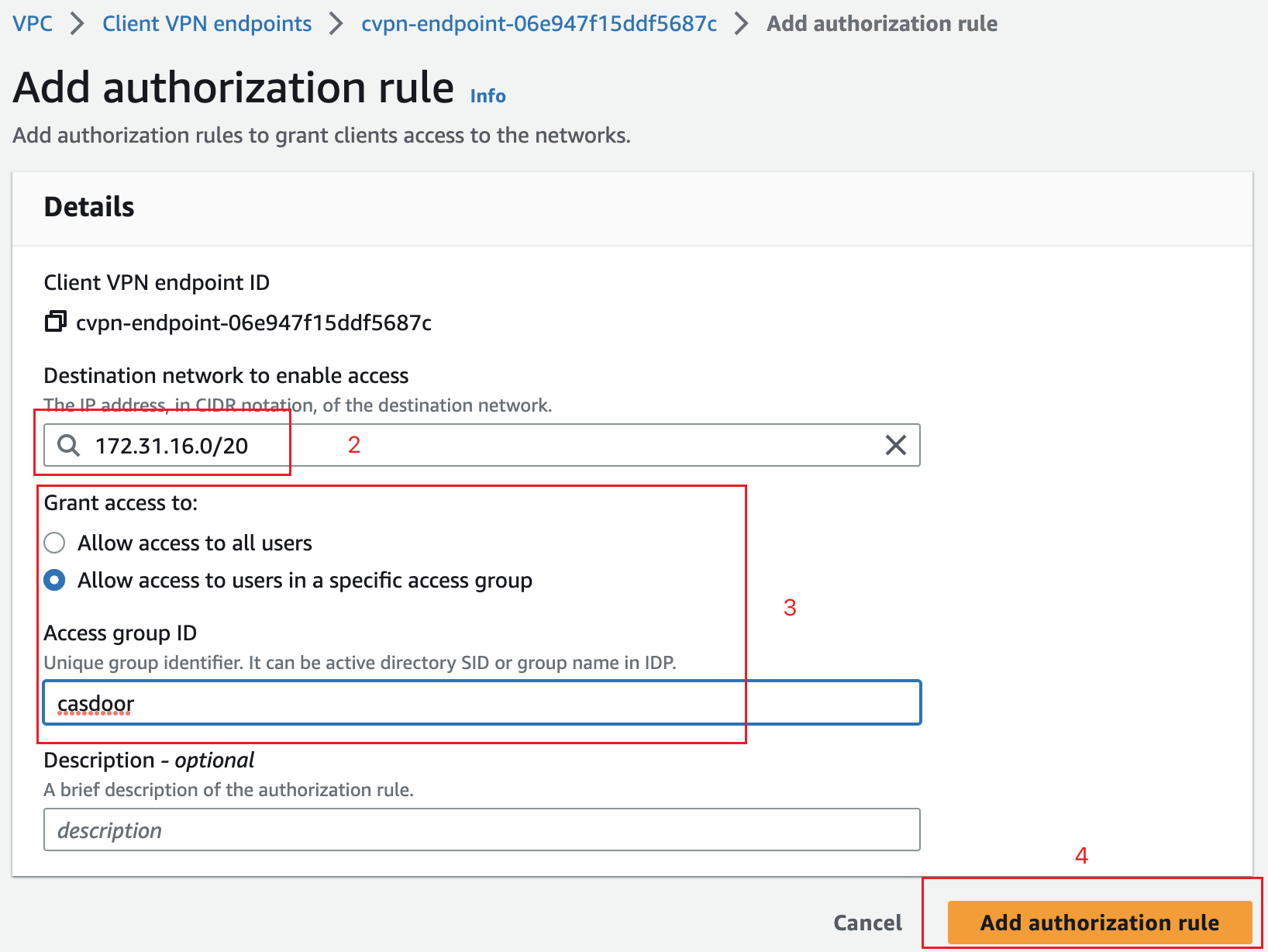
Choose the Authorization rules tab in your Client VPN options and click Add Authorize rule.
For Destination network to enable, specify the IP address of your EC2 instance created in the prerequisites. For example,
172.31.16.0/20.Under Grant access to, select Allow access to users in a specific access group. For example,
casdoor.Provide an optional description and click Add authorization rule.
Connect to Client VPN
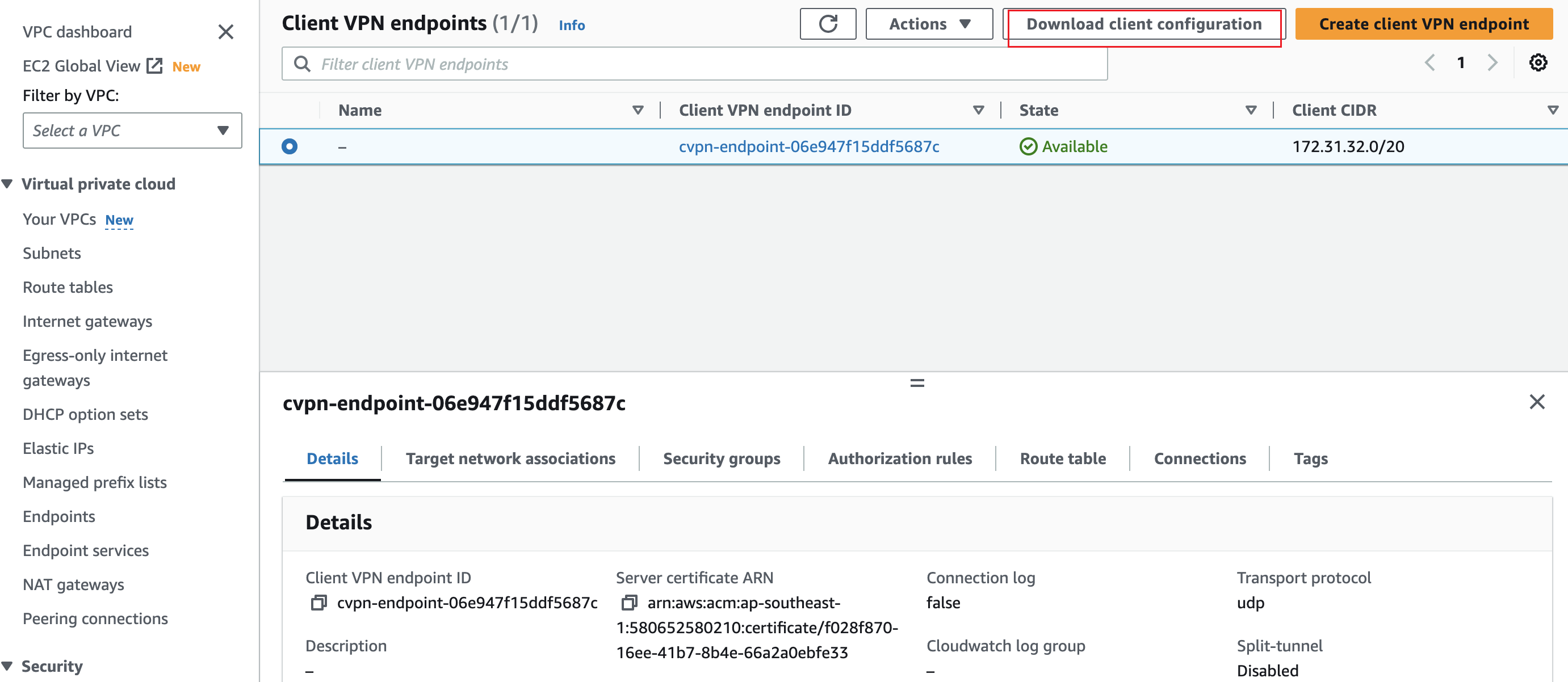
Select the Client VPN endpoint you just created. It should now be in the Available state.
Click Download Client Configuration to download the configuration profile to your desktop.
Open the AWS Client VPN desktop app on your machine.
In the top menu, select File and Manage Profiles.
Click Add Profile and point to the recently downloaded file.
You should now see the profile in the list on the AWS Client VPN software. Select it and click Connect.